USDOT Background Checks
DOT-compliant background checks with the quickest turnaround times in the industry.


Streamline the Driver Background Verification Process with Foley’s Background Screens
Order and view MVR reports, safety performance histories, DOT drug and alcohol testing, FMCSA Clearinghouse queries, CDLIS, PSP, and criminal background checks to hire safe and compliant drivers.

Hiring & DOT Compliance Peace of Mind
Hiring & DOT Compliance Peace of Mind
CDLIS & PSP Background Screens
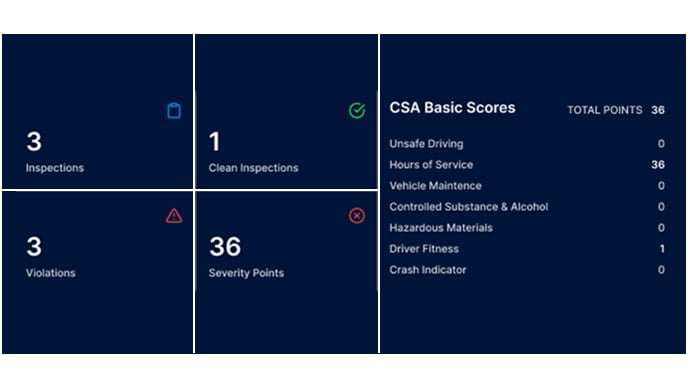
See a driver’s crash and roadside inspection record in the PSP FMCSA background check. Plus, find out about all CDLs held by the driver, including those held under an alias or former name with the CDL background check.
FMCSA Clearinghouse Queries & Drug Testing
Conduct full Clearinghouse queries to see detailed information about any drug or alcohol violations on a driver’s record, and see if your applicant has recently used substances with Foley’s DOT drug testing.
Driver Motor Vehicle Record Checks
An MVR report provides information on your applicant’s license class, status, endorsements, restrictions, and suspensions. Traffic violations and criminal convictions given while driving are also reported.
CDL Criminal Background Checks
Running criminal background screens on your driver applicant confirms their identity, reveals patterns of illegal behavior, and allows you to determine if they may pose a risk to your company’s safety and reputation.
Featured Article


Are Your USDOT Background Checks FCRA Compliant?
For many companies with commercial drivers, complying with DOT regulations is top of mind. But your background checks must also follow the strict requirements of the Fair Credit Reporting Act (FCRA).
FMCSA Background Checks for Various Industries

Truck Driver Background Check Services
Foley’s commercial truck driver background check suite not only helps your company comply with DOT and FCRA regulations, but it also helps ensure you’re hiring qualified, quality drivers to grow your fleet.

Construction CDL Driver Background Checks
You have a zero-tolerance policy for your crew. Get the peace of mind you need to make informed hiring decisions with Foley, and complete your DOT background check online in no time at all.

Background Screens for Farm Equipment Operators
By screening potential drivers, you can identify any history of reckless driving, DUI offenses, or other traffic violations that may pose a risk while operating heavy machinery. Protect your farm’s assets and reputation by checking driver applicants’ criminal background and driving records with Foley.
×
Fill out this form and a member of our team will reach out shorty.
Are you ready to experience a faster and easier background check for CDL drivers?
Fill out this form for a free demo, and see how our background check packages get new drivers on the road faster.
.png)
Whether you’re looking for a quick background check or a comprehensive DOT compliance solution, Foley can help.